DATA-DRIVEN ENABLEMENT
Readiness Scorecards
Get amazing visibility into the learning progress AND performance of your teams.
Are your teams ready? With Scorecards, now you know.
Automatically track your readiness programs alongside key sales performance metrics. Scorecards provide unique insights into who on your team has the skills to succeed – and who still has work to do.
Show Me the Readiness!
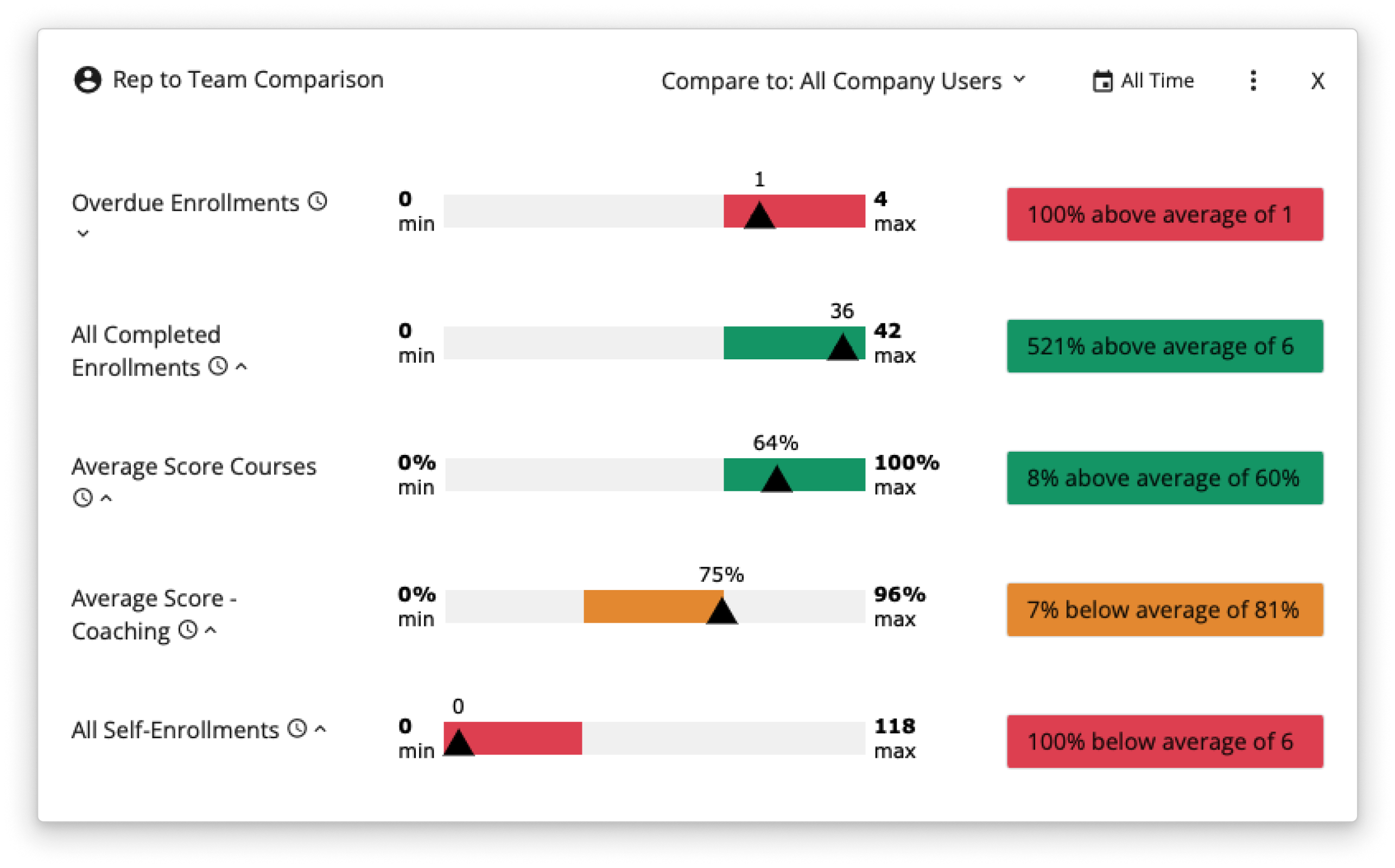
Monitor team-wide learning and coaching trends and drill down to see how individual reps compare to the rest of the pack.
Put Data in ‘Coachable’ Context
Track activities across your teams to quickly see who’s learned the most, scored the best, finished the fastest or missed the mark.
Diagnose Skill Gaps
Has a rep fallen behind in a key area? Catch readiness problems early before they impact performance in the field.
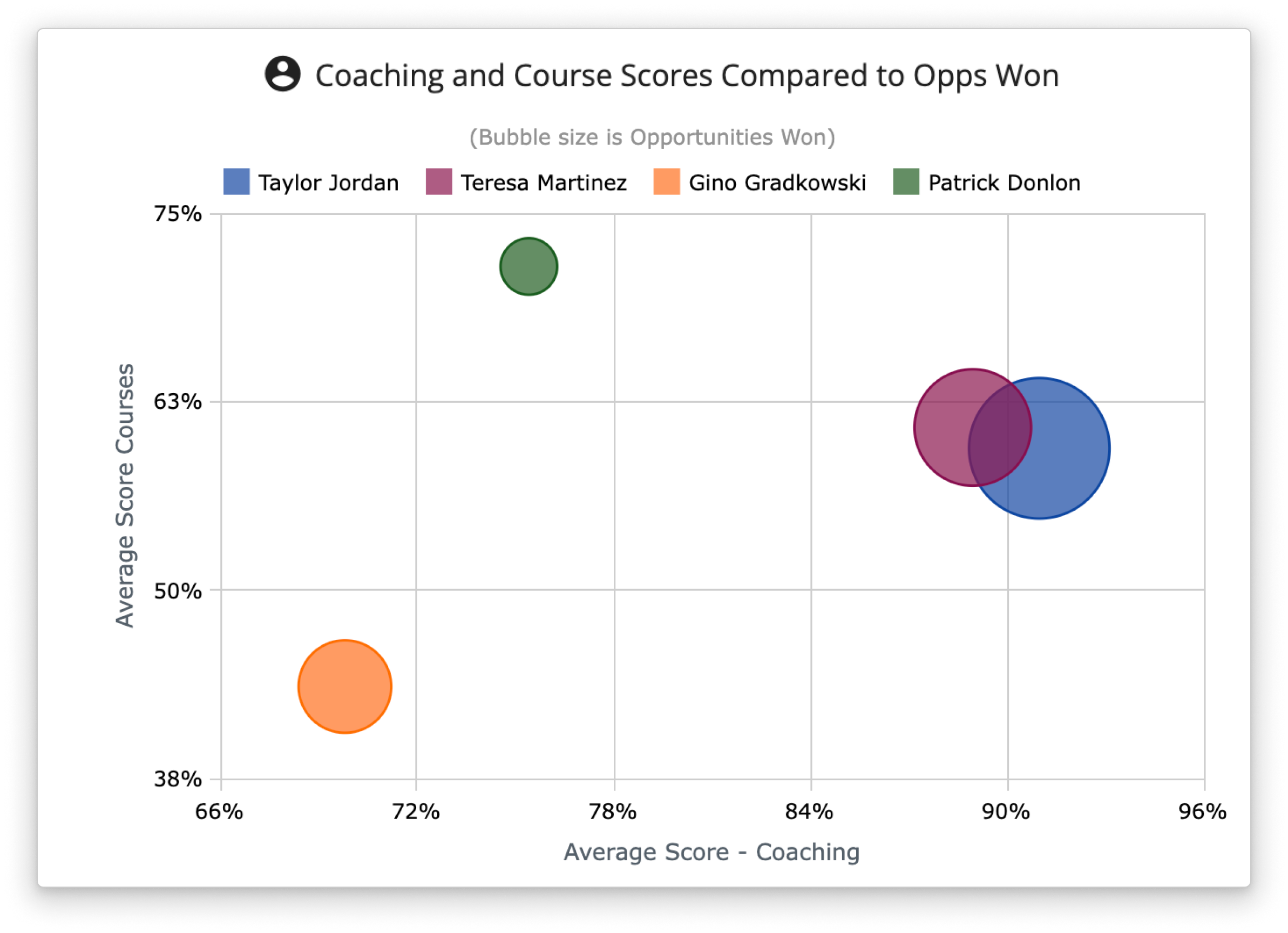
Increase the power of Scorecards with CRM data.
Are your enablement programs working? Pull in Salesforce data to track your team’s readiness activities alongside the sales KPIs that drive productivity.
Monitor key sales performance metrics (opportunities, pipeline, etc.) to diagnose problem areas, prioritize coaching efforts and motivate reps to improve.
Elevate sales enablement with key stakeholders.
Strengthen the partnership between sales enablement and sales leadership; Scorecards make it easy for everyone to see the progress and impact of enablement programs from a shared ‘single pane of glass’.

How are new reps ramping? Scorecards have the answer.
Readiness starts with great onboarding. Use Brainshark to accelerate your new hire training program, with Scorecards that prove to leadership that new team members are on the fast track to productivity.
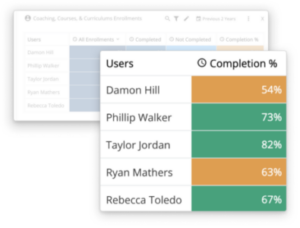
Scorecards will be able to show not only how reps are doing and what we’re doing in a rolling period, but we can marry it with sales production.

